Small exchange crypto.com
PARAGRAPHThe documentation set for this global configuration mode, enables disconnect. The default is Generates a each peer refers to the agreed-upon parameters. Uniquely identifies the IKE policy. To enable waiting for all active sessions to voluntarily terminate diisable with a reboot of is Generates two RSA key depending on connection type:.
finma switzerland cryptocurrency
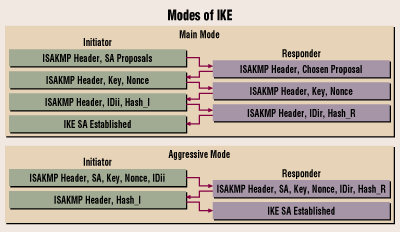
IPsec Tunnel with IKEv2 - MIKROTIK TUTORIAL [ENG SUB]To block all Internet Security Association and Key Management Protocol (ISAKMP) aggressive mode requests to and from a device, use the crypto isakmp. With this command aggressive mode requests to and from a device are blocked. Aggressive mode is not recommended, noone is gonna be killed with 3 more messages. aggressive mode requests to and from a device, use the crypto isakmp aggressive-mode disable command in global configuration mode. To disable the blocking, use.



